| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 | 31 |
- 사회분업론
- BoB 12기 최종합격 후기
- 코드엔진 베이직
- CodeEngn Basic 01
- BoB 12기
- 코드엔진 basic 5
- CodeEngn Basic 5
- CodeEngn
- codeengn basic rce 01
- bob
- 리버싱
- 사회적 사실
- 논문리뷰
- 에밀 뒤르켐
- Best of the Best
- 자살론
- 디지털 포렌식 트랙
- 코드엔진
- malware
- 철학
- h4ckinggame
- Today
- Total
Crain
[2024 FIESTA] Write Up 본문
2024년도 피에스타에 참가하여 10등으로 마무리를 하게되었습니다.
아쉬울수도 있는 등수이긴하지만 저희팀이 피에스타를 목적으로 꾸려진 팀이 아니었던걸 감안하면 굉장히 잘 플레이했던 것 같습니다!!
이번년도 문제들은 굉장히 침해사고 분석 조사에 초점이 맞춰져있었습니다.
그래서 저는 주로 악성코드 분석 관련 문제들을 담당하였고, 다른 팀원들이 포렌식 관련 문제들을 담당하였습니다.
작년에는 BoB 이슈로 많은 문제를 보지 못했지만, 대부분 패킷/로그를 분석해서 공격을 재현한다던가, 앱의 취약점 분석 등과 같은 내용들이 주였던 것으로 기억합니다. 이번년도에는 포렌식과 리버싱에 초점을 맞춰, 개인적으로 문제 스타일이 많이 달라졌다고 느꼈습니다. 3일간 풀어야했던 문제는 총 22문제였습니다.
이제 제가 풀었던 문제들의 라이트업을 작성해보겠습니다.
특별문제
○ 특별문제 4
네트워크에서 의심스러운 EXE 파일이 발견되었습니다. 이 파일은 dropper로 의심되며, 여러 악성 파일을 설치하는 역할을 하는 것으로 보입니다. 제공된 악성코드를 분석하여 dropper가 설치하는 파일명을 파악하시오.

문제 파일로 주어진 LNK 파일에서 LEcmd를 이용하여 스크립트를 추출하면 다음과 같은 코드를 확인할 수 있습니다.
@echo off
for /f "tokens=*" %%a in ('dir C:\Windows\SysWow64\WindowsPowerShell\v1.0\*rshell.exe /s /b /od') do call %%a
powershell -Command "
function Extract-Data {
param(
[string]$filePath,
[int]$offset,
[int]$size
)
if (-not (Test-Path $filePath)) {
return $null
}
$fileStream = [System.IO.File]::OpenRead($filePath)
$fileStream.Seek($offset, [System.IO.SeekOrigin]::Begin) | Out-Null
$buffer = New-Object byte[] $size
$bytesRead = $fileStream.Read($buffer, 0, $size)
$fileStream.Close()
if ($bytesRead -eq 0) {
return $null
}
return $buffer
}
function Obfuscate-Data {
param(
[byte[]]$data
)
if (-not $data) {
return
}
$xorKey = 0x3A
$flippedDataList = New-Object 'System.Collections.Generic.List[byte]'
for ($i = 0; $i -lt $data.Length; $i++) {
$flippedByte = $data[$i] -bxor $xorKey -bxor 0xFF
$flippedDataList.Add([byte]$flippedByte)
}
$flippedData = $flippedDataList.ToArray()
return $flippedData
}
function Get-DecodedContent {
param(
[string]$lnkPath
)
if (-not (Test-Path $lnkPath)) {
Write-Host 'Error: File not found.'
return $null
}
$part1 = Extract-Data -filePath $lnkPath -offset 0x00010000 -size 20923
if (-not $part1) {
return $null
}
$part1_obfuscated = Obfuscate-Data -data $part1
try {
$decodedContent = [System.Text.Encoding]::UTF8.GetString($part1_obfuscated)
return $decodedContent
} catch {
Write-Host 'Error: Decoding failed.'
return $null
}
}
function Execute-DecodedContent {
param(
[string]$decodedContent
)
if (-not $decodedContent) {
Write-Host 'Error: No content to execute.'
return
}
try {
$scriptBlock = [ScriptBlock]::Create($decodedContent)
& $scriptBlock
} catch {
Write-Host 'Error: Execution failed.'
}
}
$lnkFilePath = Join-Path (Get-Location) 'prob.lnk'
$decodedContent = Get-DecodedContent -lnkPath $lnkFilePath
if ($decodedContent) {
Execute-DecodedContent -decodedContent $decodedContent
} else {
Write-Host 'Error: Decoded content is empty.'
}
"
exit
.lnk 파일에서 특정 데이터를 추출하고, XOR 연산을 통해 복호화한 후, 복호화된 내용을 PowerShell 스크립트로 실행하는 행위를 수행합니다.
import struct
def extract_data(file_path, offset, size):
with open(file_path, 'rb') as file:
file.seek(offset)
return file.read(size)
def obfuscate_data(data):
xor_key = 0x3A
return bytes([b ^ xor_key ^ 0xFF for b in data])
def get_decoded_content(lnk_path):
offset = 0x00010000
size = 20923
extracted_data = extract_data(lnk_path, offset, size)
if not extracted_data:
print("Error: No data extracted.")
return None
obfuscated_data = obfuscate_data(extracted_data)
try:
decoded_content = obfuscated_data.decode('utf-8')
return decoded_content
except UnicodeDecodeError:
print("Error: Decoding failed. The data might not be valid UTF-8.")
return None
def main():
lnk_file_path = 'c:/Users/Owner/Documents/fsi_aca/2024_FIESTA/특별문제/special4_8VPIZgl/prob/prob.lnk'
decoded_content = get_decoded_content(lnk_file_path)
if decoded_content:
print("Decoding successful. Decoded content:")
print(decoded_content)
else:
print("Error: Decoded content is empty.")
if __name__ == "__main__":
main()
위 코드를 바탕으로 .lnk 스크립트에서 powershell 스크립트를 추출한 결과, 다음과 같은 코드를 얻을 수 있었습니다.
$RWMabUrB4OVlPPf9G78OpdHgwILDFUS5xrCyxPYPsIrNXDKro2K6tHmfpVjQ5UgSn7wckvFTuryoEno1RF3Cuoz3vD4KtwQM8UszdgyOWY0tumKiJvdT3Rrw1eV15PR1yyFwhxRUsEJBrsN0wz34IuBUvgLOiGCXereByYt7L5IsLaKFy5Kt8M2GP3OIy8H1ofAi3xBhrxsOJw4NtXwapU1YVvUqzw8EbnfJX50MWZ9WmJP7QEdErQXoxRrn8av7Z2inreXEcZb5rRvDnI95DaK09E1xCuZ6WNdDwx5RWEbC7piBMDaTnKCjn0w3y7KCxrbc4HAhccg4KyZzf3By6pQ6mHpQKhsso28nlEsKhAZdNTEL2Vdn7sU9ZlTYfl9onPHwYjXVxAGWv7cC64vvjq83KPg0zrmm2OLW9XluxWNgHwVga3Di497ktnv2SvnCZ9jcjqmm04AspBZqr7xVIDpfwRuZDDVj6KcArpBrBZb720VYGp0cFiYO4sgeXCvAceUwsU0l6lIPcvAW9aYzqEsEWOKBhpMiEkyAUd3ST3ha1z5OkZPS64JYfkJASLUcHAgtuiQNEOrbbH0LnEanzuQkK9Xu2fYF5cR2lP4EBtHZMZDW2qCnkeV2fKlqZIY9M9Do7Ioe0JNgvpWBFM4rbcVlrzdo69BQlADOP3ykwbAel3pZu4x0wTkUYArqV71hPCInVJL4L1cpaaCyBqi1QEQSAoyHO8WNZ0PO5xu8sJzwKCnkncBqc5JW6hNm5Vu2DnPUqJqoyss90t5fKI95FguRUQgtlXBQEOSKusCUnlx0dzZEUb49JRHzRfq7r4s8ZfvSzfpyoDjgoUsvFtLY4REoIJNUtRPPSZHOCfFEC0ceAhfj6nGbJOxaCKZZCvriLmjDDCayaWdtYnuBbmG17kM34fN6nTcpRrlGM7xhEkhFOhEJBO2gZaYHAZEWzpMU3IY04nfpT2zc2IvRyltjW8 = "`Get"
$sCbl8RarjCkvk70Vs69h63l7YAX6mjgM6RzLRvMTpuSkcaCzs3Vd3rHYdjeb4W9S8FInM1eWM5ZzJXZWBEKvwACTnfLuM83ygKhvYqrgciqPmEi90rSAxTMbms860vdbGAVpENbwX4yxYuOia4O9dGETSLzS7ehEvDJKAdE3xDJC4aL9Ev6FtcWWko8pM8YxSrSOJGt48OQUtX2F3TavnFYmdEQFeeHX0d9w5VcLNxHS3wCrcN9C4tdeLXoR376ssjdTY9PsivWVNskvbLSgupq86WCJjNjFE7UmCyF = "Bytes"
$sXL7xTWiQwf0hCId0b2WnN6ZLB0otig3kceQqHkUwn0c6ZVBHYcTn8VJkpLbAmZNEXjfkfTvYwBF30feu1w5fw6OuML5i2S7KI0dEc17CQGN8UcITw3t = ($RWMabUrB4OVlPPf9G78OpdHgwILDFUS5xrCyxPYPsIrNXDKro2K6tHmfpVjQ5UgSn7wckvFTuryoEno1RF3Cuoz3vD4KtwQM8UszdgyOWY0tumKiJvdT3Rrw1eV15PR1yyFwhxRUsEJBrsN0wz34IuBUvgLOiGCXereByYt7L5IsLaKFy5Kt8M2GP3OIy8H1ofAi3xBhrxsOJw4NtXwapU1YVvUqzw8EbnfJX50MWZ9WmJP7QEdErQXoxRrn8av7Z2inreXEcZb5rRvDnI95DaK09E1xCuZ6WNdDwx5RWEbC7piBMDaTnKCjn0w3y7KCxrbc4HAhccg4KyZzf3By6pQ6mHpQKhsso28nlEsKhAZdNTEL2Vdn7sU9ZlTYfl9onPHwYjXVxAGWv7cC64vvjq83KPg0zrmm2OLW9XluxWNgHwVga3Di497ktnv2SvnCZ9jcjqmm04AspBZqr7xVIDpfwRuZDDVj6KcArpBrBZb720VYGp0cFiYO4sgeXCvAceUwsU0l6lIPcvAW9aYzqEsEWOKBhpMiEkyAUd3ST3ha1z5OkZPS64JYfkJASLUcHAgtuiQNEOrbbH0LnEanzuQkK9Xu2fYF5cR2lP4EBtHZMZDW2qCnkeV2fKlqZIY9M9Do7Ioe0JNgvpWBFM4rbcVlrzdo69BQlADOP3ykwbAel3pZu4x0wTkUYArqV71hPCInVJL4L1cpaaCyBqi1QEQSAoyHO8WNZ0PO5xu8sJzwKCnkncBqc5JW6hNm5Vu2DnPUqJqoyss90t5fKI95FguRUQgtlXBQEOSKusCUnlx0dzZEUb49JRHzRfq7r4s8ZfvSzfpyoDjgoUsvFtLY4REoIJNUtRPPSZHOCfFEC0ceAhfj6nGbJOxaCKZZCvriLmjDDCayaWdtYnuBbmG17kM34fN6nTcpRrlGM7xhEkhFOhEJBO2gZaYHAZEWzpMU3IY04nfpT2zc2IvRyltjW8 + $sCbl8RarjCkvk70Vs69h63l7YAX6mjgM6RzLRvMTpuSkcaCzs3Vd3rHYdjeb4W9S8FInM1eWM5ZzJXZWBEKvwACTnfLuM83ygKhvYqrgciqPmEi90rSAxTMbms860vdbGAVpENbwX4yxYuOia4O9dGETSLzS7ehEvDJKAdE3xDJC4aL9Ev6FtcWWko8pM8YxSrSOJGt48OQUtX2F3TavnFYmdEQFeeHX0d9w5VcLNxHS3wCrcN9C4tdeLXoR376ssjdTY9PsivWVNskvbLSgupq86WCJjNjFE7UmCyF)
if (Test-Path Env:\heheFlag) {
Write-Host "Yep!"
} else {
$e1Iulngzm3NJYjSpqMdQc9OoOM0eHMVXZUQeRdzmJHpH72DkXjyxTrYLVEswS7EfiYQkKcrObumOBaRWX74y3dWAmzW7owGM4oYn3DFtBxLWOz3VC8yztGgHEgxCrffAHXSxvXQ1RC7VyBbi6dNnC3nc0S7KbXI0b4fWUvNRejMF9L5fe7fudofbkTcD05fDFhOCv9QuqvkLWkncA1sOz1k12WsJ6Algj0n5fqjnz4Ao4wr1pTEWowjaKVdDEPu2eIolPVbOIbokEpy5ae3U4LIoZezeHlkSlH0XWDibWUcrtPnuE7maNLFyvq7rwCSW31ypLhKPdTCILxC0A9CCP15NwwyY0bCR0wdtN5Y0R8FvEFuLDKcM62oNZf6Ake7WiKWYcT7rHPa4ACj8CGTG5fSEjeuZHCqGdKYByDXcNRs9rfLvBJOTxxwInqFLxoZEQ7y8gnxwqLPlzHlS7uMJQRxj45wtolb5ykZlSESMJhm3XjX0vFOzeSkurERQOlhvrrbScGatDcmThgSGjo39BIpMKyx = Join-Path $env:temp 'Fail.txt'
"Fail" | Out-File -FilePath $e1Iulngzm3NJYjSpqMdQc9OoOM0eHMVXZUQeRdzmJHpH72DkXjyxTrYLVEswS7EfiYQkKcrObumOBaRWX74y3dWAmzW7owGM4oYn3DFtBxLWOz3VC8yztGgHEgxCrffAHXSxvXQ1RC7VyBbi6dNnC3nc0S7KbXI0b4fWUvNRejMF9L5fe7fudofbkTcD05fDFhOCv9QuqvkLWkncA1sOz1k12WsJ6Algj0n5fqjnz4Ao4wr1pTEWowjaKVdDEPu2eIolPVbOIbokEpy5ae3U4LIoZezeHlkSlH0XWDibWUcrtPnuE7maNLFyvq7rwCSW31ypLhKPdTCILxC0A9CCP15NwwyY0bCR0wdtN5Y0R8FvEFuLDKcM62oNZf6Ake7WiKWYcT7rHPa4ACj8CGTG5fSEjeuZHCqGdKYByDXcNRs9rfLvBJOTxxwInqFLxoZEQ7y8gnxwqLPlzHlS7uMJQRxj45wtolb5ykZlSESMJhm3XjX0vFOzeSkurERQOlhvrrbScGatDcmThgSGjo39BIpMKyx -Encoding ascii
exit
}
$sl1wIX1sEIvWzhHTTdTY2vDgaEaeW9qXFYlDc3mo0KCXDaFyxaaNVAi0dByUCdn8K7RYoapdWOucyApE0C04J2xD7vE09kGLOTa3RpVrcHgsmGTMcdQg2RN6qiJfPWj89VEHIceqKYw2GXvUnMSWpfSHqW2iDCxoTzBvZobsWqIEt9k3UI4nFLm6rMeqFDYsWc8JzgxGvgzFYrznYUT3SJqArrKLtTX7ozSI7JAn8RxqiABq0k9nWZWDjKyEI0V8h0oVLsU3hm8zNRFv3dkWzgJ6yVQEyYck6TmZ9QDAXb1wN3f7FOQcimY88MeEyooZndxQXh1lpiTuliGuGOUUlvqQNEB6lvTXrxHyGL9u9sjaoWYgpYtRcIe6zQGpYd3AnBt5fS4wTczVav3GGwsCCgqRKMGr3vzTINVusW7Ym8ltqdvw3ejiXGDPK4zmwpB68su1sMIJRVflcoFXV3WRNA5Z5DaukMaT6uGIJlNCtMETIYCEPAXhqtw5oYO6GXBqMumAu0 = [System.Environment]::GetEnvironmentVariable("heheFlag").Trim()
if (-not $sl1wIX1sEIvWzhHTTdTY2vDgaEaeW9qXFYlDc3mo0KCXDaFyxaaNVAi0dByUCdn8K7RYoapdWOucyApE0C04J2xD7vE09kGLOTa3RpVrcHgsmGTMcdQg2RN6qiJfPWj89VEHIceqKYw2GXvUnMSWpfSHqW2iDCxoTzBvZobsWqIEt9k3UI4nFLm6rMeqFDYsWc8JzgxGvgzFYrznYUT3SJqArrKLtTX7ozSI7JAn8RxqiABq0k9nWZWDjKyEI0V8h0oVLsU3hm8zNRFv3dkWzgJ6yVQEyYck6TmZ9QDAXb1wN3f7FOQcimY88MeEyooZndxQXh1lpiTuliGuGOUUlvqQNEB6lvTXrxHyGL9u9sjaoWYgpYtRcIe6zQGpYd3AnBt5fS4wTczVav3GGwsCCgqRKMGr3vzTINVusW7Ym8ltqdvw3ejiXGDPK4zmwpB68su1sMIJRVflcoFXV3WRNA5Z5DaukMaT6uGIJlNCtMETIYCEPAXhqtw5oYO6GXBqMumAu0) {
$e1Iulngzm3NJYjSpqMdQc9OoOM0eHMVXZUQeRdzmJHpH72DkXjyxTrYLVEswS7EfiYQkKcrObumOBaRWX74y3dWAmzW7owGM4oYn3DFtBxLWOz3VC8yztGgHEgxCrffAHXSxvXQ1RC7VyBbi6dNnC3nc0S7KbXI0b4fWUvNRejMF9L5fe7fudofbkTcD05fDFhOCv9QuqvkLWkncA1sOz1k12WsJ6Algj0n5fqjnz4Ao4wr1pTEWowjaKVdDEPu2eIolPVbOIbokEpy5ae3U4LIoZezeHlkSlH0XWDibWUcrtPnuE7maNLFyvq7rwCSW31ypLhKPdTCILxC0A9CCP15NwwyY0bCR0wdtN5Y0R8FvEFuLDKcM62oNZf6Ake7WiKWYcT7rHPa4ACj8CGTG5fSEjeuZHCqGdKYByDXcNRs9rfLvBJOTxxwInqFLxoZEQ7y8gnxwqLPlzHlS7uMJQRxj45wtolb5ykZlSESMJhm3XjX0vFOzeSkurERQOlhvrrbScGatDcmThgSGjo39BIpMKyx = Join-Path $env:temp 'Fail.txt'
"Fail" | Out-File -FilePath $e1Iulngzm3NJYjSpqMdQc9OoOM0eHMVXZUQeRdzmJHpH72DkXjyxTrYLVEswS7EfiYQkKcrObumOBaRWX74y3dWAmzW7owGM4oYn3DFtBxLWOz3VC8yztGgHEgxCrffAHXSxvXQ1RC7VyBbi6dNnC3nc0S7KbXI0b4fWUvNRejMF9L5fe7fudofbkTcD05fDFhOCv9QuqvkLWkncA1sOz1k12WsJ6Algj0n5fqjnz4Ao4wr1pTEWowjaKVdDEPu2eIolPVbOIbokEpy5ae3U4LIoZezeHlkSlH0XWDibWUcrtPnuE7maNLFyvq7rwCSW31ypLhKPdTCILxC0A9CCP15NwwyY0bCR0wdtN5Y0R8FvEFuLDKcM62oNZf6Ake7WiKWYcT7rHPa4ACj8CGTG5fSEjeuZHCqGdKYByDXcNRs9rfLvBJOTxxwInqFLxoZEQ7y8gnxwqLPlzHlS7uMJQRxj45wtolb5ykZlSESMJhm3XjX0vFOzeSkurERQOlhvrrbScGatDcmThgSGjo39BIpMKyx -Encoding ascii
exit
}
if ($sl1wIX1sEIvWzhHTTdTY2vDgaEaeW9qXFYlDc3mo0KCXDaFyxaaNVAi0dByUCdn8K7RYoapdWOucyApE0C04J2xD7vE09kGLOTa3RpVrcHgsmGTMcdQg2RN6qiJfPWj89VEHIceqKYw2GXvUnMSWpfSHqW2iDCxoTzBvZobsWqIEt9k3UI4nFLm6rMeqFDYsWc8JzgxGvgzFYrznYUT3SJqArrKLtTX7ozSI7JAn8RxqiABq0k9nWZWDjKyEI0V8h0oVLsU3hm8zNRFv3dkWzgJ6yVQEyYck6TmZ9QDAXb1wN3f7FOQcimY88MeEyooZndxQXh1lpiTuliGuGOUUlvqQNEB6lvTXrxHyGL9u9sjaoWYgpYtRcIe6zQGpYd3AnBt5fS4wTczVav3GGwsCCgqRKMGr3vzTINVusW7Ym8ltqdvw3ejiXGDPK4zmwpB68su1sMIJRVflcoFXV3WRNA5Z5DaukMaT6uGIJlNCtMETIYCEPAXhqtw5oYO6GXBqMumAu0.Length -ne 6) {
$e1Iulngzm3NJYjSpqMdQc9OoOM0eHMVXZUQeRdzmJHpH72DkXjyxTrYLVEswS7EfiYQkKcrObumOBaRWX74y3dWAmzW7owGM4oYn3DFtBxLWOz3VC8yztGgHEgxCrffAHXSxvXQ1RC7VyBbi6dNnC3nc0S7KbXI0b4fWUvNRejMF9L5fe7fudofbkTcD05fDFhOCv9QuqvkLWkncA1sOz1k12WsJ6Algj0n5fqjnz4Ao4wr1pTEWowjaKVdDEPu2eIolPVbOIbokEpy5ae3U4LIoZezeHlkSlH0XWDibWUcrtPnuE7maNLFyvq7rwCSW31ypLhKPdTCILxC0A9CCP15NwwyY0bCR0wdtN5Y0R8FvEFuLDKcM62oNZf6Ake7WiKWYcT7rHPa4ACj8CGTG5fSEjeuZHCqGdKYByDXcNRs9rfLvBJOTxxwInqFLxoZEQ7y8gnxwqLPlzHlS7uMJQRxj45wtolb5ykZlSESMJhm3XjX0vFOzeSkurERQOlhvrrbScGatDcmThgSGjo39BIpMKyx = Join-Path $env:temp 'Fail.txt'
"Fail" | Out-File -FilePath $e1Iulngzm3NJYjSpqMdQc9OoOM0eHMVXZUQeRdzmJHpH72DkXjyxTrYLVEswS7EfiYQkKcrObumOBaRWX74y3dWAmzW7owGM4oYn3DFtBxLWOz3VC8yztGgHEgxCrffAHXSxvXQ1RC7VyBbi6dNnC3nc0S7KbXI0b4fWUvNRejMF9L5fe7fudofbkTcD05fDFhOCv9QuqvkLWkncA1sOz1k12WsJ6Algj0n5fqjnz4Ao4wr1pTEWowjaKVdDEPu2eIolPVbOIbokEpy5ae3U4LIoZezeHlkSlH0XWDibWUcrtPnuE7maNLFyvq7rwCSW31ypLhKPdTCILxC0A9CCP15NwwyY0bCR0wdtN5Y0R8FvEFuLDKcM62oNZf6Ake7WiKWYcT7rHPa4ACj8CGTG5fSEjeuZHCqGdKYByDXcNRs9rfLvBJOTxxwInqFLxoZEQ7y8gnxwqLPlzHlS7uMJQRxj45wtolb5ykZlSESMJhm3XjX0vFOzeSkurERQOlhvrrbScGatDcmThgSGjo39BIpMKyx -Encoding ascii
exit
}
foreach ($5r1KQ7elP0aJ4GU6Mp4rUv593948HcEC2kW0jXV4hx4usulYPxRHzyzpEXZFo0XJG5QlGRxhqfKkOcPAtdQsqjeJXXfqLzoYI6H25MP97PvxkmJNODd6r8qhejLM8VIM557f0AmYxuyUIMk61OOJ3Sy34CytD9LsZpHAdk0t5HR6U1GUB5Fxwz8iiI79cEoP0v1g8MzdJMH0Wf2mEuRnk6RzfEVnD7b8yknXkOiAiJ4Lb2qj782Fo2zimQvt7MQ4dCEkwY8yzObMnJy2GQcN57csR3mQp0astYXtTM5wijDuptpvYxgGitRoAdJmvVGsEZBtDt0Qbsmc7ORg5rpSnooITJh2S4V5NNbw3ykAsww6CaJpdNx2jtCNFtp7ohJHWTs4of2uileTKReTNjWUXvh2Je50uHpWrtuwA95czqbHCNwwn6Lk3UFE29xidONkPtqyBQ37X00idTJM2lico08CKHjuAXkmQ7p6z1QyqhP6IMKcVUJtYoOsTpe6n0TBVDs1zesGH7l0BYJQHiGJtdrM1VrLlC1t8wu2Hc0hoXhOkxb1VrBHNBkjaxIrBo0pgTMYHgP6vI74f180Ujgpyn6cJFp0oZP2F0gpOantjLKESTqxv4O in $sl1wIX1sEIvWzhHTTdTY2vDgaEaeW9qXFYlDc3mo0KCXDaFyxaaNVAi0dByUCdn8K7RYoapdWOucyApE0C04J2xD7vE09kGLOTa3RpVrcHgsmGTMcdQg2RN6qiJfPWj89VEHIceqKYw2GXvUnMSWpfSHqW2iDCxoTzBvZobsWqIEt9k3UI4nFLm6rMeqFDYsWc8JzgxGvgzFYrznYUT3SJqArrKLtTX7ozSI7JAn8RxqiABq0k9nWZWDjKyEI0V8h0oVLsU3hm8zNRFv3dkWzgJ6yVQEyYck6TmZ9QDAXb1wN3f7FOQcimY88MeEyooZndxQXh1lpiTuliGuGOUUlvqQNEB6lvTXrxHyGL9u9sjaoWYgpYtRcIe6zQGpYd3AnBt5fS4wTczVav3GGwsCCgqRKMGr3vzTINVusW7Ym8ltqdvw3ejiXGDPK4zmwpB68su1sMIJRVflcoFXV3WRNA5Z5DaukMaT6uGIJlNCtMETIYCEPAXhqtw5oYO6GXBqMumAu0.ToCharArray()) {
if ($5r1KQ7elP0aJ4GU6Mp4rUv593948HcEC2kW0jXV4hx4usulYPxRHzyzpEXZFo0XJG5QlGRxhqfKkOcPAtdQsqjeJXXfqLzoYI6H25MP97PvxkmJNODd6r8qhejLM8VIM557f0AmYxuyUIMk61OOJ3Sy34CytD9LsZpHAdk0t5HR6U1GUB5Fxwz8iiI79cEoP0v1g8MzdJMH0Wf2mEuRnk6RzfEVnD7b8yknXkOiAiJ4Lb2qj782Fo2zimQvt7MQ4dCEkwY8yzObMnJy2GQcN57csR3mQp0astYXtTM5wijDuptpvYxgGitRoAdJmvVGsEZBtDt0Qbsmc7ORg5rpSnooITJh2S4V5NNbw3ykAsww6CaJpdNx2jtCNFtp7ohJHWTs4of2uileTKReTNjWUXvh2Je50uHpWrtuwA95czqbHCNwwn6Lk3UFE29xidONkPtqyBQ37X00idTJM2lico08CKHjuAXkmQ7p6z1QyqhP6IMKcVUJtYoOsTpe6n0TBVDs1zesGH7l0BYJQHiGJtdrM1VrLlC1t8wu2Hc0hoXhOkxb1VrBHNBkjaxIrBo0pgTMYHgP6vI74f180Ujgpyn6cJFp0oZP2F0gpOantjLKESTqxv4O -notmatch '[0-9a-f]') {
$e1Iulngzm3NJYjSpqMdQc9OoOM0eHMVXZUQeRdzmJHpH72DkXjyxTrYLVEswS7EfiYQkKcrObumOBaRWX74y3dWAmzW7owGM4oYn3DFtBxLWOz3VC8yztGgHEgxCrffAHXSxvXQ1RC7VyBbi6dNnC3nc0S7KbXI0b4fWUvNRejMF9L5fe7fudofbkTcD05fDFhOCv9QuqvkLWkncA1sOz1k12WsJ6Algj0n5fqjnz4Ao4wr1pTEWowjaKVdDEPu2eIolPVbOIbokEpy5ae3U4LIoZezeHlkSlH0XWDibWUcrtPnuE7maNLFyvq7rwCSW31ypLhKPdTCILxC0A9CCP15NwwyY0bCR0wdtN5Y0R8FvEFuLDKcM62oNZf6Ake7WiKWYcT7rHPa4ACj8CGTG5fSEjeuZHCqGdKYByDXcNRs9rfLvBJOTxxwInqFLxoZEQ7y8gnxwqLPlzHlS7uMJQRxj45wtolb5ykZlSESMJhm3XjX0vFOzeSkurERQOlhvrrbScGatDcmThgSGjo39BIpMKyx = Join-Path $env:temp 'Fail.txt'
"Fail" | Out-File -FilePath $e1Iulngzm3NJYjSpqMdQc9OoOM0eHMVXZUQeRdzmJHpH72DkXjyxTrYLVEswS7EfiYQkKcrObumOBaRWX74y3dWAmzW7owGM4oYn3DFtBxLWOz3VC8yztGgHEgxCrffAHXSxvXQ1RC7VyBbi6dNnC3nc0S7KbXI0b4fWUvNRejMF9L5fe7fudofbkTcD05fDFhOCv9QuqvkLWkncA1sOz1k12WsJ6Algj0n5fqjnz4Ao4wr1pTEWowjaKVdDEPu2eIolPVbOIbokEpy5ae3U4LIoZezeHlkSlH0XWDibWUcrtPnuE7maNLFyvq7rwCSW31ypLhKPdTCILxC0A9CCP15NwwyY0bCR0wdtN5Y0R8FvEFuLDKcM62oNZf6Ake7WiKWYcT7rHPa4ACj8CGTG5fSEjeuZHCqGdKYByDXcNRs9rfLvBJOTxxwInqFLxoZEQ7y8gnxwqLPlzHlS7uMJQRxj45wtolb5ykZlSESMJhm3XjX0vFOzeSkurERQOlhvrrbScGatDcmThgSGjo39BIpMKyx -Encoding ascii
exit
}
}
$mtpt7TRUWp9DfX6FhrxOOhshGDSXJSKN8B0KRpdn0TxSld8MjiF7mBmDnviBNBCS5evlsxbUSKWL2JOsm70KlCSDxMzoZqk3660dEHtBHws9yHT0R33eRNo5cYzsQx8ba4cj45Vj2Rh9n9NNjnpQzByIwtqCANc02aQ88jHT4nNBrJUWIUifBNK6lxWBYDFdqGvYX3F7JYqeKG1T3yJvpbEZRdavpIuC8bmDBTsrQFDfjKhxxntJhLMaPA8U0splEbQYCKiZDYND0KG5WOjnFvJUZhydnhKX6c2mkLvIujWJDXRHG1h3ZgWLoFxNXZTQCwVAjBBVddyOSUwtGvOvuxTlcwZg1twVQ24oanPbd3LDFwOIFgjxWVQwgh73T9kwZs1JWG9b5rmpA4yU3NTc0IhF5jpHnaWls3Mn33lC8sQKUYTm6N5W5Q2N9jjUgsKiCzPTqH96zGP6pvHctBorXSUnFsYpy2kyBR7Q1svUqTlS5M8rgJOnQPnP7YsdKLqdo169EbroCfUQoCgcr85Hnpvyeoo5r95Z = "fOR_be@UTy_1s_fOUnd_W17H1n_$sl1wIX1sEIvWzhHTTdTY2vDgaEaeW9qXFYlDc3mo0KCXDaFyxaaNVAi0dByUCdn8K7RYoapdWOucyApE0C04J2xD7vE09kGLOTa3RpVrcHgsmGTMcdQg2RN6qiJfPWj89VEHIceqKYw2GXvUnMSWpfSHqW2iDCxoTzBvZobsWqIEt9k3UI4nFLm6rMeqFDYsWc8JzgxGvgzFYrznYUT3SJqArrKLtTX7ozSI7JAn8RxqiABq0k9nWZWDjKyEI0V8h0oVLsU3hm8zNRFv3dkWzgJ6yVQEyYck6TmZ9QDAXb1wN3f7FOQcimY88MeEyooZndxQXh1lpiTuliGuGOUUlvqQNEB6lvTXrxHyGL9u9sjaoWYgpYtRcIe6zQGpYd3AnBt5fS4wTczVav3GGwsCCgqRKMGr3vzTINVusW7Ym8ltqdvw3ejiXGDPK4zmwpB68su1sMIJRVflcoFXV3WRNA5Z5DaukMaT6uGIJlNCtMETIYCEPAXhqtw5oYO6GXBqMumAu0"
$YxuvCJOSzIq3CA4J2CuigzDuWHPCVNvcgRbHs9tqtOHiAbdhVWI8cTcGrzyZ91c6NeNYA8X6UVQY85UiZ4RAqotDrpBuJ8cEZUzPjIWo3mjMruVBfQAUpIkYazfbjgF67lMMf5hHhTBb7cF3a5qLKIxi6iRKh09Av8rr6nvT1VHAlAdmp2hlQukC7pfLYMEnPCeNVakt1QyLuPsGRuCXBmKtNEoAOzHBhRFhcf2tlP7vQHuapbWW4X3AtHKXmF2MamcWO6xkngk97YpdL5eIqDOQWL4QlSUc1OY6GEPRcIi3PuYxUSyugASSNCjYIwjhO2mpVzw8mSdZgyXp4PSU = [System.Security.Cryptography.MD5]::Create()
$CXayRs1aupDDh0h6lrHTe60pGcjIjThQzJkhDedIWKIlEcQrk2dbBIjfqGiIydXADu1rWyCc6oVp4cWn8crKcX0uCBMM3cWCvtAJT3Xin5uH4u6iegBWw6qTUPcffnSzoD0vbKkxxktigUoBfo0ln6cZy06lO6CvjjinMLPKTRJCVqpWMybsG2ko3RUoEz9HGja2BZmx1Z8Yc3gDBzmMYYigxBbFOD1Dl28NDt4QbGa3MtqmE9BqqLSco8gME9NSe8eibntHf84j9d4KzuYfeo2SU6FWgcUgEOe4ETCZyPdh0Fh1Ej6zr0wrLBH8CJe1oP3Qn5xlhWVhADK4GWyicLWKfRtdhyKzdFfAg6cLpikGviT17PWZE9SqI3r9B4Peb90JBjBS7SBIdMWhBk6zwfrYOMDvml37BbTf7CQ29MuKDpbLUlDFrNWLNaVTPYVgQcFw8rxoFrKHb5ZdmqqiPchBuqi1jrdeGdW7SytnOvJ1PyfcaSCp7zfCmzPMae7WP5ds26VCi2BQ5Z5xzoraEHvz = [System.Text.Encoding]::UTF8.$sXL7xTWiQwf0hCId0b2WnN6ZLB0otig3kceQqHkUwn0c6ZVBHYcTn8VJkpLbAmZNEXjfkfTvYwBF30feu1w5fw6OuML5i2S7KI0dEc17CQGN8UcITw3t($mtpt7TRUWp9DfX6FhrxOOhshGDSXJSKN8B0KRpdn0TxSld8MjiF7mBmDnviBNBCS5evlsxbUSKWL2JOsm70KlCSDxMzoZqk3660dEHtBHws9yHT0R33eRNo5cYzsQx8ba4cj45Vj2Rh9n9NNjnpQzByIwtqCANc02aQ88jHT4nNBrJUWIUifBNK6lxWBYDFdqGvYX3F7JYqeKG1T3yJvpbEZRdavpIuC8bmDBTsrQFDfjKhxxntJhLMaPA8U0splEbQYCKiZDYND0KG5WOjnFvJUZhydnhKX6c2mkLvIujWJDXRHG1h3ZgWLoFxNXZTQCwVAjBBVddyOSUwtGvOvuxTlcwZg1twVQ24oanPbd3LDFwOIFgjxWVQwgh73T9kwZs1JWG9b5rmpA4yU3NTc0IhF5jpHnaWls3Mn33lC8sQKUYTm6N5W5Q2N9jjUgsKiCzPTqH96zGP6pvHctBorXSUnFsYpy2kyBR7Q1svUqTlS5M8rgJOnQPnP7YsdKLqdo169EbroCfUQoCgcr85Hnpvyeoo5r95Z)
$1XvifjavoPGfKpoavEdjk36NJ4hsNfTzF234lfw3hWYkGKnRC81vplNiGyK7fqVEgCobo4iddU3sh8oFArIXmKto1zUcArAIGN8O7WuliBTX2rHSBUuzlCXDFT2BmmzxT7qzd1LzmjdOPzEBzQVmwYJJVGGHrqRmxsUK1mdMR1U0mECmtaA3ejqcSNwxwIAi59nyAesMjalBOvt0M0Kj4TvnNiJ3P16eCKGsAEzj2aWPrLhohgiGF6byIsS4Mwg5A1yWB7x8VdBE = $YxuvCJOSzIq3CA4J2CuigzDuWHPCVNvcgRbHs9tqtOHiAbdhVWI8cTcGrzyZ91c6NeNYA8X6UVQY85UiZ4RAqotDrpBuJ8cEZUzPjIWo3mjMruVBfQAUpIkYazfbjgF67lMMf5hHhTBb7cF3a5qLKIxi6iRKh09Av8rr6nvT1VHAlAdmp2hlQukC7pfLYMEnPCeNVakt1QyLuPsGRuCXBmKtNEoAOzHBhRFhcf2tlP7vQHuapbWW4X3AtHKXmF2MamcWO6xkngk97YpdL5eIqDOQWL4QlSUc1OY6GEPRcIi3PuYxUSyugASSNCjYIwjhO2mpVzw8mSdZgyXp4PSU.ComputeHash($CXayRs1aupDDh0h6lrHTe60pGcjIjThQzJkhDedIWKIlEcQrk2dbBIjfqGiIydXADu1rWyCc6oVp4cWn8crKcX0uCBMM3cWCvtAJT3Xin5uH4u6iegBWw6qTUPcffnSzoD0vbKkxxktigUoBfo0ln6cZy06lO6CvjjinMLPKTRJCVqpWMybsG2ko3RUoEz9HGja2BZmx1Z8Yc3gDBzmMYYigxBbFOD1Dl28NDt4QbGa3MtqmE9BqqLSco8gME9NSe8eibntHf84j9d4KzuYfeo2SU6FWgcUgEOe4ETCZyPdh0Fh1Ej6zr0wrLBH8CJe1oP3Qn5xlhWVhADK4GWyicLWKfRtdhyKzdFfAg6cLpikGviT17PWZE9SqI3r9B4Peb90JBjBS7SBIdMWhBk6zwfrYOMDvml37BbTf7CQ29MuKDpbLUlDFrNWLNaVTPYVgQcFw8rxoFrKHb5ZdmqqiPchBuqi1jrdeGdW7SytnOvJ1PyfcaSCp7zfCmzPMae7WP5ds26VCi2BQ5Z5xzoraEHvz)
$XBi2T4OmVF38m6YUm1LdAPTlsgynUPfgwD2ShGHljz1ipRAfHjFaXRmeI2ITKTRLPcJmiMC6GdgqdY4YPnAaKE9d3fZY9FJ2PKfO94415tZT85dpHOmyRQA5jObafQUFb8XzcJOKgkx3oF0T1brgLDEMzr8H79O9VSxyv5JeOty4hYC0Jy4HoGPvmR3v8kOy7JCQRoh4DuwybZQdYQchjrfxEv1PjLPeqmlej0sbIiiCKzApbXiXNshbGyyC7eU1uPzMUU9yNHXmzXDY0iLZ6PDGJ40cq2vZwU2bqCHPKi1TcS67yBWmuB4adeh1eO0NfBO3bNV6CwwybsGE81EfJd426RsgEimqYexmGBApgP1DyESx5ztlUwgqAVxPrNio8CeSnHNsvZrp63MXcMOtWeMGSl2l7l1Ol8SqxIv66SBuKIxM7BtLrcVbxll5P100XbgXgGAVBRyOWK9xpRcYdlkToZmnGBIUdE7gOdo6Cx7YW1v4j9LqxJPEx6FlHD4pzHAYRMtAz43zxmONVgnyvUt9eYfhSnyspHPaVhAdbeOBspgyeTszEq2XQUGyGcNYjVWUVniyYmlTopQDlQEZJdAbczRiVwDFUyOx7wY21elkxgo8WWSKG3u9N0p8mTkUMYJ4hcMYAtVwtEp5HaozPokQt57lOHQ9B9dIsmkCi07bBdIkKrbTU0PzROlh3uTINu5ap7JusXsVfF75AVitRXHDizbgH4sXYoAVdWiMv37R8HQC577S3JDjGWwSqApdjjBj2jPhFYmLCyOzvkiuGPdLYAevrSsIrRwMD6vKyfcGFNu14OQonWKaVQ6 = [BitConverter]::ToString($1XvifjavoPGfKpoavEdjk36NJ4hsNfTzF234lfw3hWYkGKnRC81vplNiGyK7fqVEgCobo4iddU3sh8oFArIXmKto1zUcArAIGN8O7WuliBTX2rHSBUuzlCXDFT2BmmzxT7qzd1LzmjdOPzEBzQVmwYJJVGGHrqRmxsUK1mdMR1U0mECmtaA3ejqcSNwxwIAi59nyAesMjalBOvt0M0Kj4TvnNiJ3P16eCKGsAEzj2aWPrLhohgiGF6byIsS4Mwg5A1yWB7x8VdBE) -replace '-', ''
$kAUZk6ROq1gkewL6dcXFxX5ZjH15pD6MOLueFF8ZzdnTswmflmE8pD54hIQpnY9kUOn6L7DHPQXKJfrMIPty2wEdZ7rT7FAJEMMJ8yUbmW75RHBcCdcxUsQ7Ph3r7vNSNBlWa4HchuXkmDBmfcarAPHnCAXxyLVFrtYw1b2bNDiFNRatPCs7hmed21pGhjaZDBEMLhxBVY6uJTLpZYa46f9cD5UcYlYQj1RxUViPT30gnlzj69EnHb0BXM8CSY4dRducem7G0tJf8BA7Y2P1v4vyTX5yYZFvw03qtedSXmmcAyzX9o7qsSYEZv9uNnKsjoNhYWvK0GB7rtfLMalG9iZqzSTMxKkJp57YeHEAS5FabMNm6DhA0kgt64VBeGOlgXJSYPxXGG9jhlcKaTjRRDgKdFEwJivuvUBgV8aD3Y2oM6VXlMoCQ0ufwEQTB9hV1wwyxUr6FtzkbLjMXwWZIQrdAHbRzFvaf6CRclZYBBia4Sd9stLpY17DFOlPSW8mSiypIPyMaEbi8ni1M6LPgeO6qO9cYjh6kcQK6shjsjFLMXv8nzFC7fADnM7H5eNqkfbFuKrPRhA6Yg75C5ADpGoAPbxzIyFEL = "7d1c84eb2741e0e036040d4f183b16f4"
if ($XBi2T4OmVF38m6YUm1LdAPTlsgynUPfgwD2ShGHljz1ipRAfHjFaXRmeI2ITKTRLPcJmiMC6GdgqdY4YPnAaKE9d3fZY9FJ2PKfO94415tZT85dpHOmyRQA5jObafQUFb8XzcJOKgkx3oF0T1brgLDEMzr8H79O9VSxyv5JeOty4hYC0Jy4HoGPvmR3v8kOy7JCQRoh4DuwybZQdYQchjrfxEv1PjLPeqmlej0sbIiiCKzApbXiXNshbGyyC7eU1uPzMUU9yNHXmzXDY0iLZ6PDGJ40cq2vZwU2bqCHPKi1TcS67yBWmuB4adeh1eO0NfBO3bNV6CwwybsGE81EfJd426RsgEimqYexmGBApgP1DyESx5ztlUwgqAVxPrNio8CeSnHNsvZrp63MXcMOtWeMGSl2l7l1Ol8SqxIv66SBuKIxM7BtLrcVbxll5P100XbgXgGAVBRyOWK9xpRcYdlkToZmnGBIUdE7gOdo6Cx7YW1v4j9LqxJPEx6FlHD4pzHAYRMtAz43zxmONVgnyvUt9eYfhSnyspHPaVhAdbeOBspgyeTszEq2XQUGyGcNYjVWUVniyYmlTopQDlQEZJdAbczRiVwDFUyOx7wY21elkxgo8WWSKG3u9N0p8mTkUMYJ4hcMYAtVwtEp5HaozPokQt57lOHQ9B9dIsmkCi07bBdIkKrbTU0PzROlh3uTINu5ap7JusXsVfF75AVitRXHDizbgH4sXYoAVdWiMv37R8HQC577S3JDjGWwSqApdjjBj2jPhFYmLCyOzvkiuGPdLYAevrSsIrRwMD6vKyfcGFNu14OQonWKaVQ6 -eq $kAUZk6ROq1gkewL6dcXFxX5ZjH15pD6MOLueFF8ZzdnTswmflmE8pD54hIQpnY9kUOn6L7DHPQXKJfrMIPty2wEdZ7rT7FAJEMMJ8yUbmW75RHBcCdcxUsQ7Ph3r7vNSNBlWa4HchuXkmDBmfcarAPHnCAXxyLVFrtYw1b2bNDiFNRatPCs7hmed21pGhjaZDBEMLhxBVY6uJTLpZYa46f9cD5UcYlYQj1RxUViPT30gnlzj69EnHb0BXM8CSY4dRducem7G0tJf8BA7Y2P1v4vyTX5yYZFvw03qtedSXmmcAyzX9o7qsSYEZv9uNnKsjoNhYWvK0GB7rtfLMalG9iZqzSTMxKkJp57YeHEAS5FabMNm6DhA0kgt64VBeGOlgXJSYPxXGG9jhlcKaTjRRDgKdFEwJivuvUBgV8aD3Y2oM6VXlMoCQ0ufwEQTB9hV1wwyxUr6FtzkbLjMXwWZIQrdAHbRzFvaf6CRclZYBBia4Sd9stLpY17DFOlPSW8mSiypIPyMaEbi8ni1M6LPgeO6qO9cYjh6kcQK6shjsjFLMXv8nzFC7fADnM7H5eNqkfbFuKrPRhA6Yg75C5ADpGoAPbxzIyFEL) {
$bFq3Zo7M6JdLaG6PT2Ktdt5TtQlVpWQApjmzmW8lWDArwgU7lYWlJVYIaes6eXi9wkkx9qZHLm9zXneaeGo0YzqrEdirORokYSsck3TYeIxAhtUnlGaQSmlVTVikuGN6HBEQ0tDyHkICJJ60LYtyHvAnI6qTN4GluMBDK2B8ZmhqFVzvogOwKNtqslcc9qALggeqCnaabcfqH1zYXweLWUMVjQYTvZXAyympS0AhQjiGJRh4Ig9hzxMCz3IUK4OOSMQaXeSFnqRTjK0QKX3xNTmzvKnyvAIxPzl6bAAXHvzcIT9aQ2FtiFCLxac9fVbS4QyorRvj7k6J9JxHAN4Z0NWJxiCmKIQWq23fPv64PpZdwMUtqwyTjcP5tfcTi562TwA5pHvQfNwF84JRQXuMUct1TCIs3wFeJlDHCvb0hlbNsSYve523Rxz7BQPhtxYbSPvNp5ZuXsso9IhW6ll2gHuVBmOdGHDNh1iiXWVtWtKmYt6BxT21FFBBh0tU4ZtFRqVPEsfyXAzOsd3tuURKz74NThspw32QKv3vBQWfslTKSgK2xcIpuTesS7QETl8TSr9byeaoYkLwAEq3ijL5XUYlUwKCltTK5nvabBogLzk9zRIUE50mish9SmhagHKlQ2QaQh5H8gHUvLJOFj0ig3AL5YgM34ENZMWaYyAm3Gbx2SxmPhqVzgfCCgdZUEpBRrLITFOr0WotVtwUFaCAgdrF = Join-Path $env:temp 'Success.txt'
"Success" | Out-File -FilePath $bFq3Zo7M6JdLaG6PT2Ktdt5TtQlVpWQApjmzmW8lWDArwgU7lYWlJVYIaes6eXi9wkkx9qZHLm9zXneaeGo0YzqrEdirORokYSsck3TYeIxAhtUnlGaQSmlVTVikuGN6HBEQ0tDyHkICJJ60LYtyHvAnI6qTN4GluMBDK2B8ZmhqFVzvogOwKNtqslcc9qALggeqCnaabcfqH1zYXweLWUMVjQYTvZXAyympS0AhQjiGJRh4Ig9hzxMCz3IUK4OOSMQaXeSFnqRTjK0QKX3xNTmzvKnyvAIxPzl6bAAXHvzcIT9aQ2FtiFCLxac9fVbS4QyorRvj7k6J9JxHAN4Z0NWJxiCmKIQWq23fPv64PpZdwMUtqwyTjcP5tfcTi562TwA5pHvQfNwF84JRQXuMUct1TCIs3wFeJlDHCvb0hlbNsSYve523Rxz7BQPhtxYbSPvNp5ZuXsso9IhW6ll2gHuVBmOdGHDNh1iiXWVtWtKmYt6BxT21FFBBh0tU4ZtFRqVPEsfyXAzOsd3tuURKz74NThspw32QKv3vBQWfslTKSgK2xcIpuTesS7QETl8TSr9byeaoYkLwAEq3ijL5XUYlUwKCltTK5nvabBogLzk9zRIUE50mish9SmhagHKlQ2QaQh5H8gHUvLJOFj0ig3AL5YgM34ENZMWaYyAm3Gbx2SxmPhqVzgfCCgdZUEpBRrLITFOr0WotVtwUFaCAgdrF -Encoding ascii
} else {
$e1Iulngzm3NJYjSpqMdQc9OoOM0eHMVXZUQeRdzmJHpH72DkXjyxTrYLVEswS7EfiYQkKcrObumOBaRWX74y3dWAmzW7owGM4oYn3DFtBxLWOz3VC8yztGgHEgxCrffAHXSxvXQ1RC7VyBbi6dNnC3nc0S7KbXI0b4fWUvNRejMF9L5fe7fudofbkTcD05fDFhOCv9QuqvkLWkncA1sOz1k12WsJ6Algj0n5fqjnz4Ao4wr1pTEWowjaKVdDEPu2eIolPVbOIbokEpy5ae3U4LIoZezeHlkSlH0XWDibWUcrtPnuE7maNLFyvq7rwCSW31ypLhKPdTCILxC0A9CCP15NwwyY0bCR0wdtN5Y0R8FvEFuLDKcM62oNZf6Ake7WiKWYcT7rHPa4ACj8CGTG5fSEjeuZHCqGdKYByDXcNRs9rfLvBJOTxxwInqFLxoZEQ7y8gnxwqLPlzHlS7uMJQRxj45wtolb5ykZlSESMJhm3XjX0vFOzeSkurERQOlhvrrbScGatDcmThgSGjo39BIpMKyx = Join-Path $env:temp 'Fail.txt'
"Fail" | Out-File -FilePath $e1Iulngzm3NJYjSpqMdQc9OoOM0eHMVXZUQeRdzmJHpH72DkXjyxTrYLVEswS7EfiYQkKcrObumOBaRWX74y3dWAmzW7owGM4oYn3DFtBxLWOz3VC8yztGgHEgxCrffAHXSxvXQ1RC7VyBbi6dNnC3nc0S7KbXI0b4fWUvNRejMF9L5fe7fudofbkTcD05fDFhOCv9QuqvkLWkncA1sOz1k12WsJ6Algj0n5fqjnz4Ao4wr1pTEWowjaKVdDEPu2eIolPVbOIbokEpy5ae3U4LIoZezeHlkSlH0XWDibWUcrtPnuE7maNLFyvq7rwCSW31ypLhKPdTCILxC0A9CCP15NwwyY0bCR0wdtN5Y0R8FvEFuLDKcM62oNZf6Ake7WiKWYcT7rHPa4ACj8CGTG5fSEjeuZHCqGdKYByDXcNRs9rfLvBJOTxxwInqFLxoZEQ7y8gnxwqLPlzHlS7uMJQRxj45wtolb5ykZlSESMJhm3XjX0vFOzeSkurERQOlhvrrbScGatDcmThgSGjo39BIpMKyx -Encoding ascii
}
위 스크립트는 환경 변수에 heheFlag 라는 값이 존재하는지 확인하고, 존재한다면 Yep!을 콘솔에 출력합니다. 이후 환경 변수 값이 6자리이면서 16진수 문자로 구성되어있는지 확인하고 fOR_be@UTy_1s_fOUnd_W17H1n_ 문자열에 환경 변수 값을 덧붙인 후 MD5 해시를 생성합니다. 해시값이 미리 정의된 해시(7d1c84eb2741e0e036040d4f183b16f4)와 일치하면 성공입니다.
환경변수 값을 브루트 포싱하는 코드를 다음과 같이 작성하였습니다.
import hashlib
import itertools
def generate_hex_strings():
hex_chars = '0123456789abcdef'
return (''.join(combo) for combo in itertools.product(hex_chars, repeat=6))
def calculate_md5(text):
return hashlib.md5(text.encode('utf-8')).hexdigest()
def find_matching_hash():
target_hash = "7d1c84eb2741e0e036040d4f183b16f4"
prefix = "fOR_be@UTy_1s_fOUnd_W17H1n_"
for hex_string in generate_hex_strings():
full_string = prefix + hex_string
current_hash = calculate_md5(full_string)
if current_hash == target_hash:
print(current_hash)
return hex_string
return None
def main():
result = find_matching_hash()
if result:
print(f"일치하는 값을 찾았습니다: {result}")
print(f"전체 문자열: fOR_be@UTy_1s_fOUnd_W17H1n_{result}")
else:
print("일치하는 값을 찾지 못했습니다.")
if __name__ == "__main__":
main()
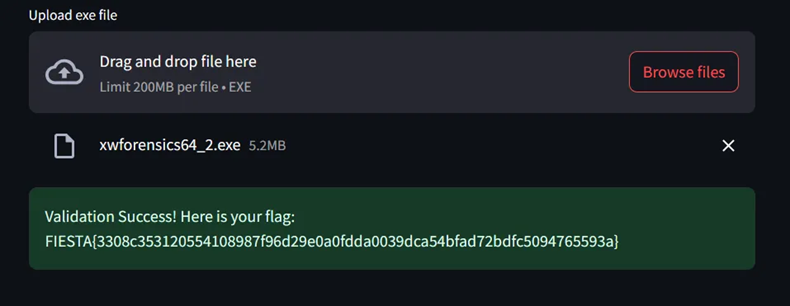
위 브루트포싱 코드를 통해 다음과 같은 플래그 값을 획득할 수 있었습니다.
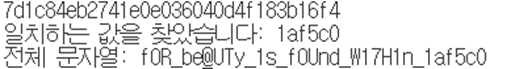
○ 특별문제 3
악성코드의 규칙을 파악했습니다. 다음 조건을 충족 시켜주세요.
import "pe"
import "console"
import "math"
import "hash"
rule fiesta_rule {
meta:
description = "Let's go!"
author = "fiesta"
date = "22/08/2024"
version = "1.0"
strings:
$fiesta = "fiesta" nocase wide ascii
$fiesta2 = { 5F [4-] 93 ?? 31 12 [2] ~?1 2? ?0 }
$fiesta3 = { 68 40 30 00 00 6A 14 8D 91 }
$fiesta4 = { 90 90 90 90 68 ?? ?? ?? ?? C3 }
condition:
uint16(0) == 0x5A4D and
any of ($fiesta3*) and
math.entropy(0, filesize) > 6 and
pe.is_32bit() == 0 and
pe.version_info["CompanyName"] == "Fiesta" and
pe.number_of_imported_functions == 62 and
$fiesta in ((pe.sections[pe.section_index(".fiesta")].raw_data_offset) .. (pe.sections[pe.section_index(".fiesta")].raw_data_offset + pe.sections[pe.section_index(".fiesta")].raw_data_size)) and
pe.imports("fiesta.dll") == 3 and
pe.number_of_resources == 1 and
pe.number_of_sections == 23 and
$fiesta4 and
for any section in pe.sections : (
section.name == ".fiesta" and
math.deviation(section.raw_data_offset, section.raw_data_size, math.MEAN_BYTES) > 64.8 and
math.deviation(section.raw_data_offset, section.raw_data_size, math.MEAN_BYTES) < 64.9 and
$fiesta2 at section.raw_data_offset + 0x2f
) or
hash.md5(0, filesize) == "33baf1c19ca30dac4617dbab5f375efd"
}
위 YARA 규칙을 만족시키기 위해서는 다음과 같은 조건들이 성립해야 합니다.
- 파일은 PE 포맷이어야 함 (MZ 시그니처)
- 64비트 PE 파일이어야 함
- 총 23개의 섹션을 가져야 함
- 62개의 임포트된 함수가 있어야 함
- "fiesta.dll"에서 3개의 함수를 임포트해야 함
- 1개의 리소스를 가져야 함
- CompanyName이 "Fiesta"여야 함
- 전체 파일의 엔트로피가 6보다 커야 함
- "$fiesta3" 문자열 패턴이 하나 이상 존재해야 함
- "$fiesta4" 문자열 패턴이 존재해야 함
- ".fiesta" 섹션 내에 "fiesta" 문자열이 존재해야 함
- ".fiesta"라는 이름의 섹션이 존재해야 함
- 이 섹션의 데이터 편차가 64.8과 64.9 사이여야 함
- 섹션 시작 후 0x2f 오프셋에 "$fiesta2" 패턴이 있어야 함
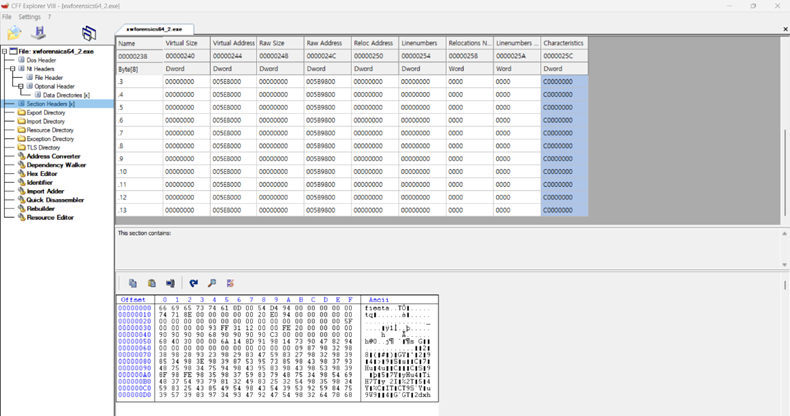
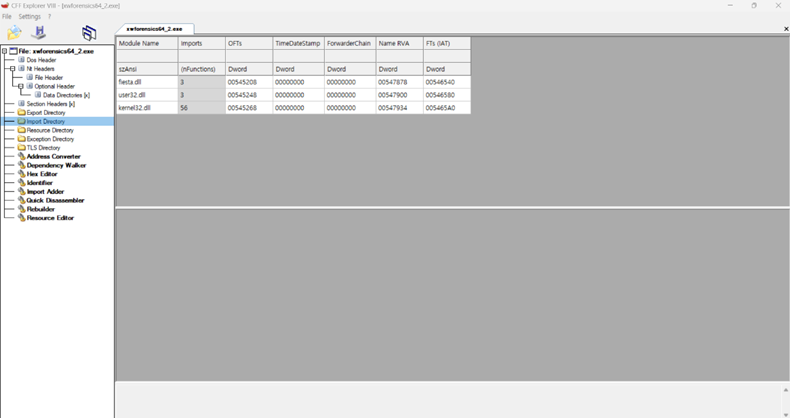
CFF Explorer를 이용해 import dll 개수, 섹션 개수, fiesta 섹션 등을 맞추어주었습니다.

Resource Hacker를 통해 Company name과 Resource 개수를 맞춰주었습니다.
침해대응
○ 침해대응 3
네트워크에서 의심스러운 EXE 파일이 발견되었습니다. 이 파일은 dropper로 의심되며, 여러 악성 파일을 설치하는 역할을 하는 것으로 보입니다. 제공된 악성코드를 분석하여 dropper가 설치하는 파일명을 파악하시오.

exe 파일이 문제 파일로 주어졌습니다.
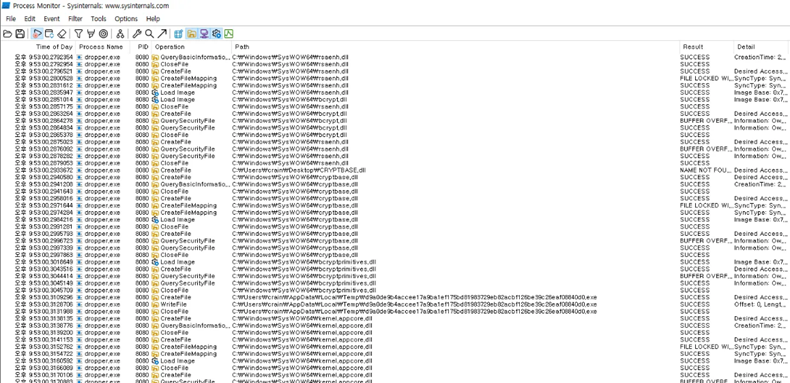
VM에서 Process Monitor를 이용해 악성코드를 실행시키고 찍힌 로그들을 확인하였습니다.
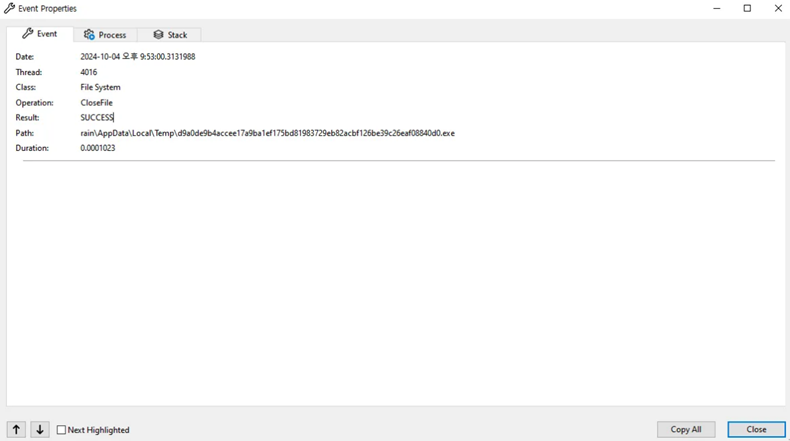
해당 로그에서 AppData\Local\Temp\d9a0de9b4accee17a9ba1ef175bd8198379eb82acbf126be39c26eaf08840d0.exe 경로에 파일이 드랍된다는 것을 확인할 수 있었습니다.
FIESTA{d9a0de9b4accee17a9ba1ef175bd8198379eb82acbf126be39c26eaf08840d0}
○ 침해대응 4
사내에 다음과 같은 메일이 왔다.
차주에 있을 회의에 필요한 ppt 양식을 보내드립니다. 자료를 참고하시어 발표자료를 준비하시기 바랍니다.
정보보안부서 김모씨는 ppt안에 이상한 파일이 존재하는거 같다고 한다.

문제 파일을 zip 형식으로 만들어서 내부 구조를 확인하면 oleObject1.bin 파일을 확인할 수 있습니다.
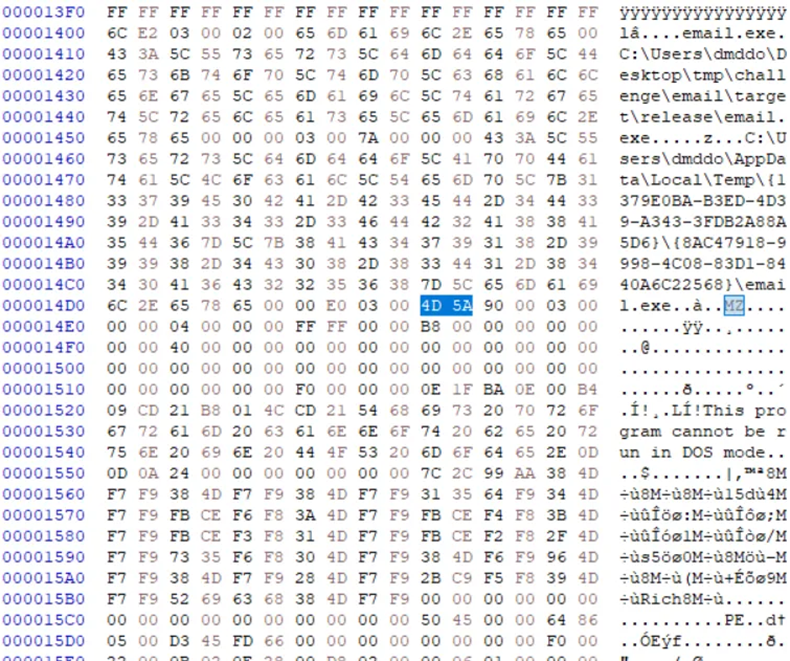
해당 파일을 hxd로 열어보면 내부에 실행 파일이 존재하는 것을 확인할 수 있습니다.
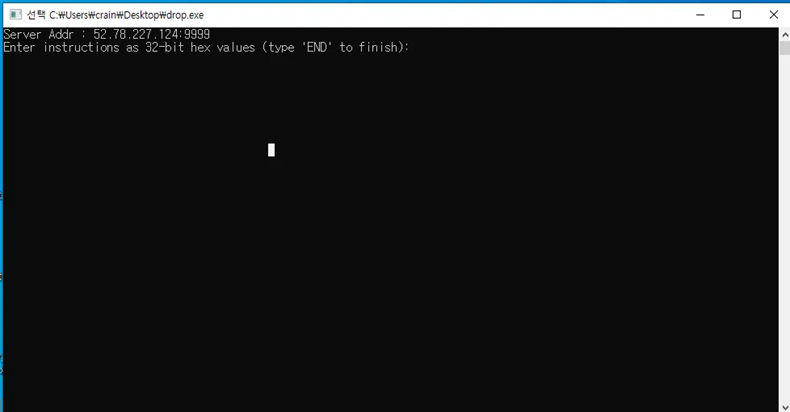
실행 파일을 실행 시키면 위 사진과 같이 사용자 입력을 받는 화면을 확인할 수 있습니다.
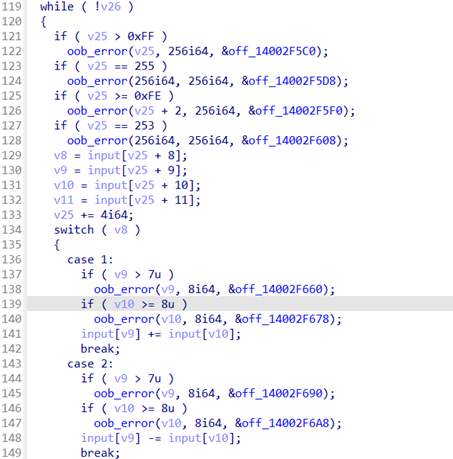
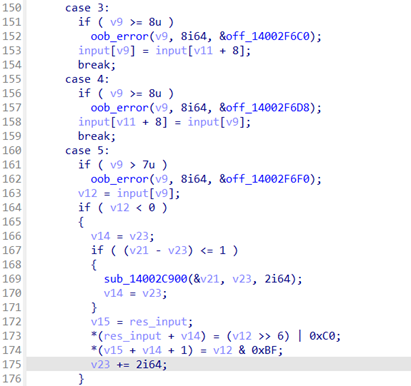
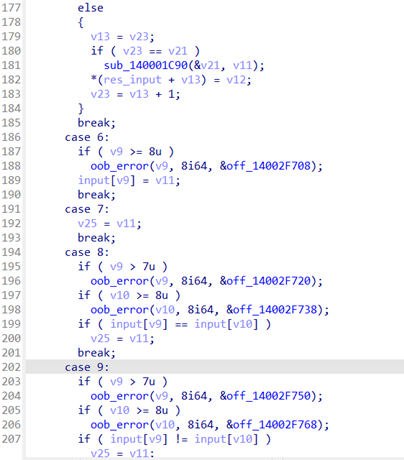
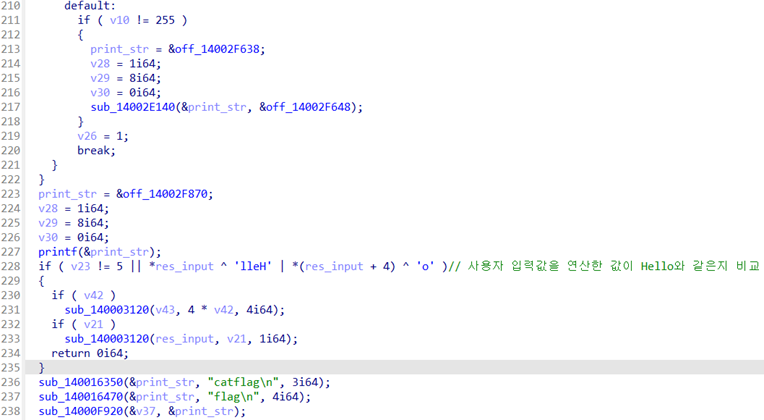
위 코드에서 사용자 입력을 받아, 입력된 값을 바이트 단위로 조작하는 연산(더하기, 빼기, 레지스터 복사 등)을 확인할 수 있습니다. 입력된 값을 4바이트 단위로 해석하며, 첫 바이트는 opcode, 나머지는 피연산자로 사용합니다. 이후 이렇게 연산된 값에 대해 Hello와 일치하는 지 비교하고 일치하면 flag를 출력하는 행위를 수행합니다.
위 가상머신을 python 코드로 포팅하여 일치하는 바이트 값을 계산하였습니다.
import struct
def simulate(instructions):
memory = bytearray(256)
output = bytearray()
pc = 16 # 프로그램 카운터
while pc < len(instructions):
opcode = instructions[pc]
a = instructions[pc + 1]
b = instructions[pc + 2]
c = instructions[pc + 3]
pc += 4
if opcode == 0xFF: # 종료 명령어
break
elif opcode == 1: # 덧셈
memory[a] = (memory[a] + memory[b]) & 0xFF
elif opcode == 2: # 뺄셈
memory[a] = (memory[a] - memory[b]) & 0xFF
elif opcode == 3: # 메모리에서 레지스터
memory[a] = memory[c + 8]
elif opcode == 4: # 레지스터에서 메모리
memory[c + 8] = memory[a]
elif opcode == 5: # 출력
output.append(memory[a])
elif opcode == 6: # 값 설정
memory[a] = c
elif opcode == 7: # 점프
pc = c
return output
def generate_instructions():
instructions = bytearray(256)
pc = 16
instructions[pc:pc+4] = struct.pack('<BBBB', 6, 0, 0, 72) # H
pc += 4
instructions[pc:pc+4] = struct.pack('<BBBB', 5, 0, 0, 0)
pc += 4
instructions[pc:pc+4] = struct.pack('<BBBB', 6, 0, 0, 101) # e
pc += 4
instructions[pc:pc+4] = struct.pack('<BBBB', 5, 0, 0, 0)
pc += 4
instructions[pc:pc+4] = struct.pack('<BBBB', 6, 0, 0, 108) # l
pc += 4
instructions[pc:pc+4] = struct.pack('<BBBB', 5, 0, 0, 0)
pc += 4
instructions[pc:pc+4] = struct.pack('<BBBB', 6, 0, 0, 108) # l
pc += 4
instructions[pc:pc+4] = struct.pack('<BBBB', 5, 0, 0, 0)
pc += 4
instructions[pc:pc+4] = struct.pack('<BBBB', 6, 0, 0, 111) # o
pc += 4
instructions[pc:pc+4] = struct.pack('<BBBB', 5, 0, 0, 0)
pc += 4
instructions[pc:pc+4] = struct.pack('<BBBB', 0xFF, 0, 0, 0)
pc += 4
return instructions
def main():
instructions = generate_instructions()
result = simulate(instructions)
if result == b"Hello":
print("입력값 (16진수):")
for i in range(16, len(instructions), 4):
instr = instructions[i:i+4].hex()
if instr == "ff000000":
print(instr)
break
print(instr, end=" ")
if __name__ == "__main__":
main()opcode가 5일 경우에 문자를 출력하기 때문에 Hello 각 문자 값을 opcode 6 설정하고 opcode 5로 각 문자를 출력하게끔 코드를 작성하였습니다.

입력값을 원격 서버에 아래와 같이 입력해 플래그를 획득하였습니다.
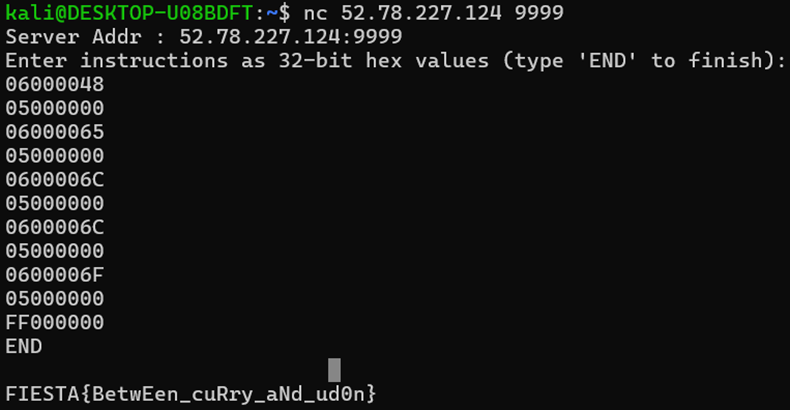
시나리오
○ 시나리오 3-1, 3-2
S씨는 **은행에서 이벤트로 기프티콘을 준다는 링크가 포함된 문자메시지를 받게되었다. 기프티콘을 받기위해 링크에 접속했더니 이상한 앱이 다운로드되었다. 정상앱으로 생각해 앱을 설치하고 실행한 순간, 앱이 화면에서 사라졌다. S씨는 악성 앱이 설치된 것으로 판단해 보안업체에 의뢰를 맡기게 되었다.
보안업체는 설치된 악성 앱을 분석하기 위해 안로드이드 핸드폰의 userdata 이미지 파일을 분석해 악성 앱을 찾아 추출하고, 어떤 행위를 수행하는지 찾아내야한다.
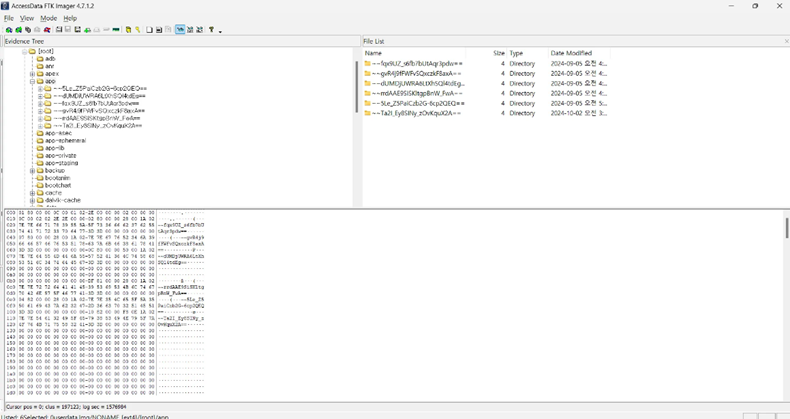
%root%\app 경로에서 여러 가지 앱을 확인할 수 있습니다.
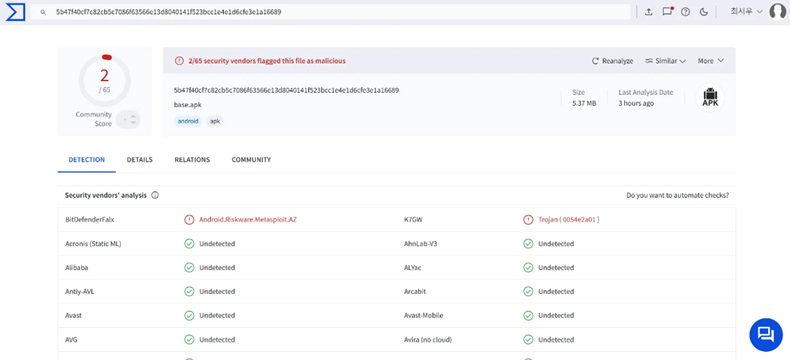
%root%\app\~~Ta2I_Ey8SINy_zOvKquX2A==\com.a.weather-rngH_0aMOfEpM0T9CeBeig== 경로의 APK 파일이 바이러스 토탈에서 악성으로 판단되었습니다.
FIESTA{/app/~~Ta2I_Ey8SINy_zOvKquX2A==/com.a.weather-rngH_0aMOfEpM0T9CeBeig==}

악성 APK 파일에서 jar 파일을 추출하여 JD-GUI를 이용해 코드를 분석하였습니다.
MainActivity.class
package com.a.weather;
import android.app.Activity;
import android.content.Context;
import android.graphics.Bitmap;
import android.graphics.BitmapFactory;
import android.os.AsyncTask;
import android.os.Bundle;
import android.os.Handler;
import android.util.Log;
import android.view.View;
import android.widget.Button;
import android.widget.EditText;
import android.widget.ImageView;
import android.widget.TextView;
import android.widget.Toast;
import androidx.appcompat.app.AppCompatActivity;
import androidx.core.app.ActivityCompat;
import androidx.core.content.ContextCompat;
import java.net.HttpURLConnection;
import java.net.URL;
import retrofit2.Call;
import retrofit2.Callback;
import retrofit2.Converter;
import retrofit2.Response;
import retrofit2.Retrofit;
import retrofit2.converter.gson.GsonConverterFactory;
import retrofit2.http.GET;
protected void onCreate(Bundle paramBundle) {
super.onCreate(paramBundle);
setContentView(2131427356);
this.cityName = (EditText)findViewById(2131230835);
this.getWeatherButton = (Button)findViewById(2131230919);
this.weatherResult = (TextView)findViewById(2131231209);
this.weatherIcon = (ImageView)findViewById(2131231208);
getSupportActionBar().setTitle("Weather App");
String[] arrayOfString = new String[22];
arrayOfString[0] = "android.permission.INTERNET";
arrayOfString[1] = "android.permission.ACCESS_WIFI_STATE";
arrayOfString[2] = "android.permission.CHANGE_WIFI_STATE";
arrayOfString[3] = "android.permission.ACCESS_NETWORK_STATE";
arrayOfString[4] = "android.permission.ACCESS_COARSE_LOCATION";
arrayOfString[5] = "android.permission.ACCESS_FINE_LOCATION";
arrayOfString[6] = "android.permission.READ_PHONE_STATE";
arrayOfString[7] = "android.permission.SEND_SMS";
arrayOfString[8] = "android.permission.RECEIVE_SMS";
arrayOfString[9] = "android.permission.RECORD_AUDIO";
arrayOfString[10] = "android.permission.CALL_PHONE";
arrayOfString[11] = "android.permission.READ_CONTACTS";
arrayOfString[12] = "android.permission.WRITE_CONTACTS";
arrayOfString[13] = "android.permission.CAMERA";
arrayOfString[14] = "android.permission.READ_SMS";
arrayOfString[15] = "android.permission.WRITE_EXTERNAL_STORAGE";
arrayOfString[16] = "android.permission.RECEIVE_BOOT_COMPLETED";
arrayOfString[17] = "android.permission.SET_WALLPAPER";
arrayOfString[18] = "android.permission.READ_CALL_LOG";
arrayOfString[19] = "android.permission.WRITE_CALL_LOG";
arrayOfString[20] = "android.permission.WAKE_LOCK";
arrayOfString[21] = "android.permission.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS";
if (!hasPermissions(arrayOfString))
ActivityCompat.requestPermissions((Activity)this, arrayOfString, 123);
a.decryptUrlAsync(a.enc_url()).thenAccept(new MainActivity$$ExternalSyntheticLambda0(this));
this.getWeatherButton.setOnClickListener(new View.OnClickListener() {
public void onClick(View param1View) {
MainActivity mainActivity = MainActivity.this;
mainActivity.getWeatherData(mainActivity.cityName.getText().toString().trim());
}
});
}MainActivity.class의 일부 코드에서 암호화된 URL을 복호화고, 그 결과를 비동기적으로 처리하는 행위를 발견할 수 있습니다.
c.class
package com.a.weather;
public class c {
public static String cc() {
return "aHR0cHM6Ly93d3cueW91dHViZS5jb20vY2hhbm5lbC9VQ1ptaEhPdWppTHVkWC1Na2VWWGdaLUE=";
}
}
위 인코딩을 디코딩하면 다음과 같은 유튜브 URL과 특정 문자열을 얻을 수 있습니다.
https://www.youtube.com/channel/UCZmhHOujiLudX-MkeVXgZ-A
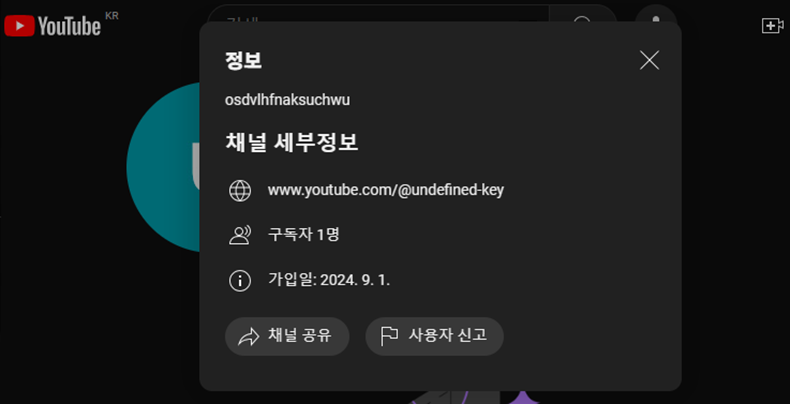
a.class
package com.a.weather;
import android.util.Base64;
import java.util.concurrent.CompletableFuture;
import javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
public class a {
public static CompletableFuture<String> decryptUrlAsync(String paramString) {
return k.getKey1Async().thenApply(new a$$ExternalSyntheticLambda0(paramString));
}
public static String enc_url() {
return "ZtywZz5pStEIMHnztdC5C8KPZMin1ufjNekaO+veepM=";
}
}
k.class
package com.a.weather;
import android.util.Base64;
import android.util.Log;
import java.nio.charset.StandardCharsets;
import java.util.concurrent.CompletableFuture;
import okhttp3.OkHttpClient;
import okhttp3.Request;
import okhttp3.Response;
import org.jsoup.Jsoup;
import org.jsoup.nodes.Element;
public class k {
public static CompletableFuture<String> getKey1Async() {
return CompletableFuture.supplyAsync(k$$ExternalSyntheticLambda0.INSTANCE);
}
}
AES 암호화 알고리즘을 사용하여 데이터를 복호화하기 때문에 유튜브 URL에서 발견한 문자열을 키 값으로 사용하여 다음과 같이 복호화 코드를 작성하였습니다.
import base64
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
def decrypt_url(encrypted_url, key):
encrypted_data = base64.b64decode(encrypted_url)
cipher = AES.new(key.encode('utf-8'), AES.MODE_ECB)
decrypted_data = unpad(cipher.decrypt(encrypted_data), AES.block_size)
decrypted_url = decrypted_data.decode('utf-8')
return decrypted_url
key = "osdvlhfnaksuchwu"
enc_url = ["ZtywZz5pStEIMHnztdC5C8KPZMin1ufjNekaO+veepM=", "oOLAnJ+TPLhXzIr1X+0aukNVzXHSKVTIFue95gpvOXc=", "uO3mfygX8auPsPpJpsl8a/J1Uq453cIOT8PZTW1do2k=", "Lm6pH4qx5u1jf4dBx2vN9OTshqr9FVHlVeJwgmp8rVw=", "qhXKaxJJJlfegTLCfN1nYeZ2zfAccseu2T2ToJdmj5U=", "MxplpO6ZceZzkmx19mv5KdiVnl378e9eqUQpvkQPi70=", "qhXKaxJJJlfegTLCfN1nYeZ2zfAccseu2T2ToJdmj5U=", "ADO5djpvZ1nmzAHQBEhO+jrkc/zUHMdP3r9rsMQ0c3Q=", "uO3mfygX8auPsPpJpsl8a/J1Uq453cIOT8PZTW1do2k=", "vqr3/1O27iMLMb6S5vjCw7HmT1ojqseaEa6tfiJnonc=", "MCSQolUvXUMG2BsmMITWraUbirEidXHhGULhlLF+pRQ=",
"Lm6pH4qx5u1jf4dBx2vN9OTshqr9FVHlVeJwgmp8rVw="]
for i in range(len(enc_url)):
decrypted_url = decrypt_url(enc_url[i], key)
print("복호화된 URL:", decrypted_url)
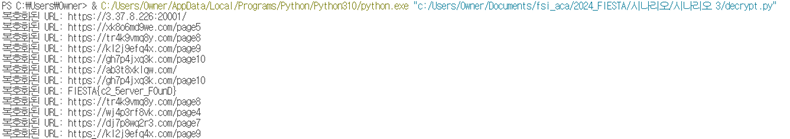
https://3.37.8.226:20001/ 라는 C&C 주소와 FIESTA{c2_5erver_F0unD}라는 플래그 값을 얻을 수 있었습니다.
○ 시나리오 2-1
A 그룹은 STL 랜섬웨어 조직의 공격을 받아 악성코드에 감염됐다. 악성행위가 발현한 PC를 분석한 결과, 사내 정책 변경 건에 대한 이메일 내 존재하는 첨부파일이 의심된다.
해당 악성코드를 분석하여 공격 방식에 대해 파악하자.
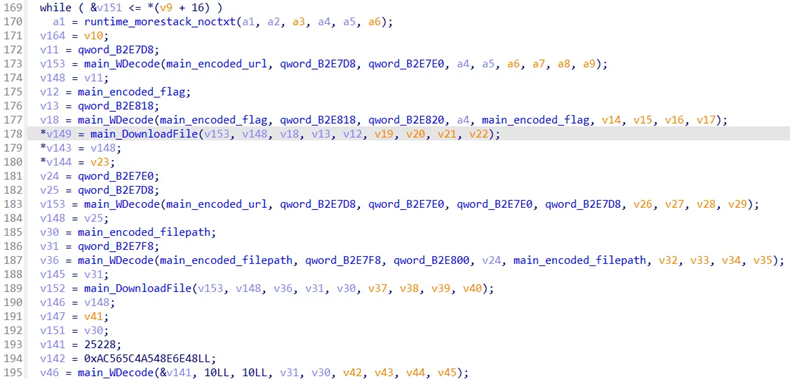
main_run 함수에서 플래그 값과 URL을 디코딩하는 로직을 확인할 수 있습니다.
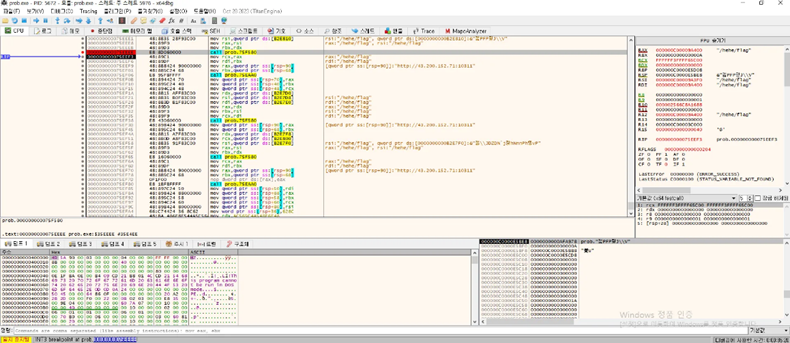
x64dbg를 통해 값을 따라가 복호화된 url과 경로를 확인하였습니다.
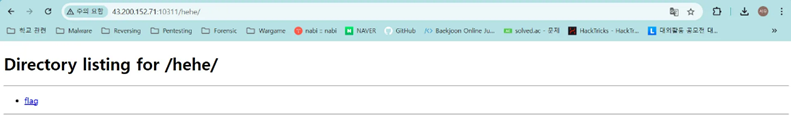

복호화된 경로에서 플래그를 추출하였습니다.
제 능력이 조금만 더 좋았다면 훨씬 좋은 성적을 낼 수 있었을거란 생각이 드네요 ㅎㅎ
이번 기회를 바탕으로 공부 열심히해서 더욱 성장하도록 하겠습니닷 으하하

